TrustFactor
Multifactor
Authentication Solution
Robust and secure authentication solution designed to provide enhanced security and user confidence in transactional operations.
TrustFactor is a robust and secure MFA (Multifactor Authentication) solution designed for integrating authentication and authorization functionalities into your product. TrustFactor provides a superior alternative to SMS codes or traditional code-based 2FA systems. TrustFactor enhances the security of existing passwords by adding biometric protection, without relying on shared secrets and ensuring cryptographic security.
Practical Benefits
Enhanced Security and Efficiency
• Replaces traditional methods like SMS, matrix cards, or hard tokens with advanced second-level authorization; • Offers passwordless logins and a secure communication channel with users;Cost-Effective Solution
• Eliminates the need for additional hardware and removes SMS-related costs;Versatile Functionality
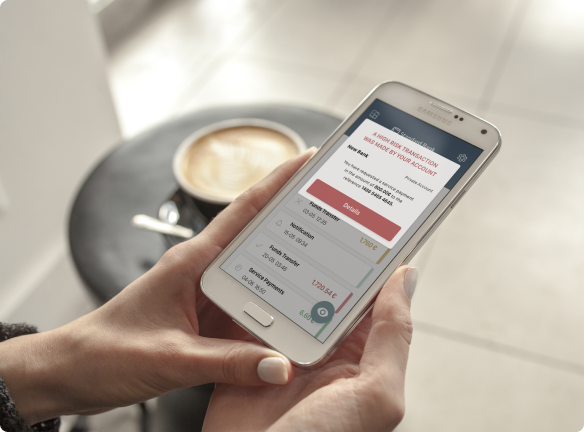
• User Notifications & Operations Decision Flow: Manage user alerts and support both generic and client-defined workflows; • Contextual Approval: Provides detailed push notifications for transaction review and approval, with adaptable risk alerts and multi-device support; • Pre-Defined Schema: Ensures secure transactions and smooth system updates by adhering to client-set standards;
Enhancing the security of accounts and systems, and it is widely used in corporate environments, financial services, and online platforms that require a high level of security.

Strong Authentication
TrustFactor combines MFA with cryptographic key-pair mechanisms
Only authorized users can access sensitive transactions
TrustFactor uses a Trust On First Use (TOFU) model for the enrollment process
By leveraging advanced encryption techniques and strong authentication mechanisms, TrustFactor ensures the integrity and authenticity of user transactions, protecting against unauthorized access and fraud
MFA involves using multiple methods to verify a user's identity before granting access to a specific resource. When only one form of authentication (like usernames and passwords) is used, resources are susceptible to breaches. By adding other authentication factors, security is significantly strengthened, reducing the likelihood of cyberattacks.

Information that only the authorized user knows, such as passwords, PINs, passphrases, answers to security questions... Note: Security questions are generally not recommended, as attackers can often bypass them with relative ease.

Authentication is based on something the user has in their possession, such as a mobile phone, physical token, smart card... Note: This could involve using a code generated by an app on the phone or received through an automated call.

It is the most secure of the three, involves verifying identities through biometric traits that are inherent to the individual. Examples include: Fingerprint scanning, Facial recognition, Retinal scanning, Voice recognition...

Recently, this additional factor has gained importance. It ensures that operational attempts by a user are not originating from widely differing or impractical locations.

For a comparison with other authenticators, check out the 'Compared to Other Authenticators' Section below.

With smartphone use at 80-85% globally, TrustFactor works seamlessly across devices, supporting over 55% of all internet traffic from mobile

No passwords for attackers to steal, reducing the need to store sensitive data and minimizing the risk of breaches

Easily add biometric authentication to any device (Windows, Mac, Android, iOS). Biometric data stays secure on the local device, managed by the operating system

No manual input like codes or usernames is needed to authenticate secure online operations

Each device has a unique digital certificate to identify and verify the user, preventing denial of authorization

Can be installed in more than one Smartphone and integrate multiple accounts

TrustFactor encrypts all data, ensuring only the correct device can decrypt and access sensitive information

Provides full transaction records with timestamps and cryptographic signatures for legal validation and dispute resolution
TrustFactor can be embedded into a Client App, which is not possible with any of the other options, enhancing the user experience (UX). TrustFactor stands out in the authentication landscape by addressing several limitations of traditional methods, as outlined below:

SIM Cloning: Intercept SMS messages on ilegitimate phone - Rogue BTS: GSM fake antenas intercept comms - Malicious Apps: Intercept SMS on the legitimate phone

Blind Authentication, no transaction context

Blind Authentication, no transaction context - Can be stolen (no extra key required)

Can be stolen or copied (no extra key required) - Matrix encryption model is not secure (many short keys, easy internal attacks)

Requires the purchase of expensive additional hardware - High cost to offer to customers - Not practical - Not intuitive - Can be lost

TrustFactor’s comprehensive approach eliminates these vulnerabilities, offering a more secure, cost-effective, and user-friendly solution
| Topic | TrustFactor | SMS Tokens | Soft Tokens | Hard Tokens | Security Key | Matrix Card |
|---|---|---|---|---|---|---|
| MFA: Knowledge Factor |  |  | ||||
| MFA: Possession Factor |  |  |  |  |  |  |
| MFA: Inheritance Factor |  |  | ||||
| MFA: Location Factor |  | |||||
| Phishing-Safe | Zero Input |  | |||||
| UI/UX Customization |  | |||||
| Allow Embedded Solution |  | |||||
| BackOffice Solution |  | |||||
| CAPEX: Investment Cost | $$ | $$ | $ | $$$ | $$$ | $ |
| OPEX: Usage Cost | $$ | $$ | $ | $$ | $$ | $$ |
| Cost per Authentication |  | |||||
| NOTE: Cost estimated based on 300 k users and 10 M authentication per Year. | ||||||

To get started, simply download the app and register with CyanBank (our Homebanking demo). That’s it! You’ll be able to explore the entire process on your own—completely intuitive and free. No need to request access. However, if you need assistance or additional information, we’re more than happy to help.